Attacking the Industry 4.0 via the BACnet protocol
In the era of digital transformation and Industry 4.0, the so-called Fourth Industrial Revolution, cybersecurity has become a crucial priority not only for traditional Information Technology (IT) systems, but also for those that manage industrial operations, which are widely used in the Operational Technology (OT) world. The growth in collective interest is due, in large part, to the rapid adoption of new cutting-edge technologies that are blurring the line between IT and OT. However, this new structural and design configuration is the main cause of the emerging vulnerabilities.
Internship context
This article is the result of my thesis work, carried out in collaboration with Betrusted, part of the Intré Group, with whom, over a period of six months, I’ve studied, analysed and deepened my understanding of the OT world and the vulnerabilities that affect these complex environments.
Penetration testing of OT environments faces unique challenges that are missing from IT environments. These challenges include the diversity of technologies employed, real-time operational constraints, high security concerns associated with critical infrastructure, and limited availability of technical documentation. These factors require highly specialised skills and meticulous planning to effectively mitigate security risks. Thanks to the study carried out, it was possible to investigate three key aspects, specifically:
- An analysis of the major global threats affecting these environments, examining emerging vulnerabilities and common attack strategies.
- An overview of existing penetration testing frameworks, highlighting their limitations and strengths in relation to relevant technologies.
- Implementing targeted attacks on purpose-built test systems and replication to real-world, internet-exposed industrial environments.
Basic Concepts
Operational technology covers a wide range of hardware and software used to monitor, control and manage physical processes in industrial environments, such as factories, power plants and critical infrastructures. In this context, a key role is played by Industrial Control Systems (ICS), a wide range of devices such as Programmable Logic Controllers (PLC), Supervisory Control and Data Acquisition (SCADA) and Distributed Control Systems (DCS). Specifically, OT security is defined as a set of practices and technologies designed to protect people, resources and information, monitor and/or control physical devices, processes and events, and initiate state changes in business systems.
The challenges in ICS security
Traditionally, the cybersecurity of these environments was not necessary because the systems were not connected to the Internet and, therefore, were not exposed to external threats. With the propagation of digital innovation initiatives for the convergence of OT and IT, systems have become more interconnected, exposing industrial networks to new and sophisticated cybersecurity threats. IT and OT networks are often kept separate, with a duplication of monetary and practical efforts to ensure security, sometimes at the expense of transparency. These new IT/OT networks are not able to monitor what is happening across the attack surface. Typically, the management of OT and IT networks is entrusted to two different units, resulting in the presence of two teams dedicated to the security of the infrastructure that can each protect half of it. This can make it difficult to identify the boundaries of the attack surface, because these separate teams do not know what is connected to their network. In addition, to being difficult to manage efficiently, IT/OT networks have huge security gaps.
With the advent of the Industrial Internet of Things (IIoT) and the increasing integration between IT and OT networks, ICSs are evolving to take advantage of global connectivity. However, this transformation has also led to new challenges, particularly with regard to security. During the last CS3STHLM – Stockholm International Summit on Cyber-Security in SCADA and Industrial Control Systems, the growing online exposure of ICS devices was highlighted. A significant number of industrial devices, including sensors, PLCs and SCADA systems, are publicly accessible on the Internet, often without adequate security measures. The reasons behind this trend are manifold. The ability to manage infrastructures remotely offers advantages in terms of operational efficiency and maintenance cost savings, allowing a technician to monitor and intervene on systems from anywhere. However, this practice carries significant risks, including vulnerability to cyber attacks. Malicious actors can exploit weak configurations, default or missing credentials, and lack of network segmentation to access and compromise critical systems.
To mitigate these risks, a multi-layered security strategy for ICSs is essential. Recommended practices include segregating OT networks from IT networks, implementing industrial firewalls, using intrusion detection systems (IDSs), and enforcing access management policies based on the principle of least privilege. In addition, it is crucial to raise awareness of IT security among technicians and staff by promoting regular system and credential update practices. In a context where industrial systems are increasingly interconnected, maintaining a balance between accessibility and security is a crucial challenge to ensure business continuity and the protection of critical infrastructures. ICSs will continue to evolve, playing a key role in the digitisation of industry, but this evolution will have to be accompanied by adequate attention to emerging risks and vulnerabilities.
These elements will be further elaborated and analysed in the chapter.
OT/ICS protocols
In the OT context, the protocols that are used are generally different from those that are normally found in an IT context. This differentiation stems from the need to develop protocols that can guarantee the security, reliability and efficiency of industrial networks. Compared to IT protocols, OT protocols face unique challenges, such as the need to operate in real time, the reliability of communication in harsh environmental conditions and interoperability between heterogeneous devices. As technologies advance, the convergence between the OT and IT worlds is becoming increasingly relevant, leading to the emergence of new protocols and the modernization of existing ones, with a focus on IT security and remote management capabilities. However, the increasing interconnection between business and industrial systems has exposed the protocols to new risks. Due to the lack of built-in authentication and encryption, additional security measures had to be developed, such as the use of secure communication gateways and industrial firewalls.
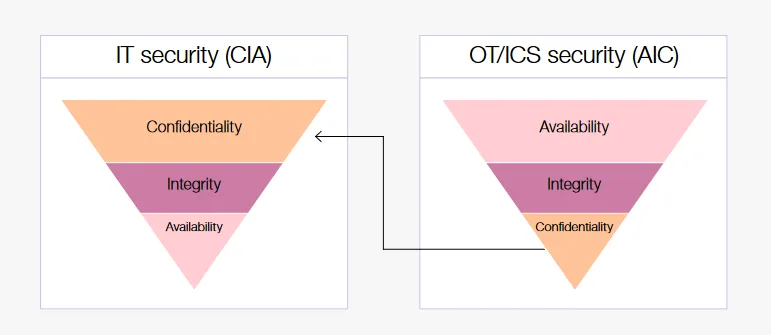
Unlike IT protocols, which emphasise scalability and security through the use of standards such as TCP/IP and SSL/TLS, OT protocols are designed to ensure integrity and business continuity even in the presence of failures. OT/ICS network architectures are therefore often segmented and protected by specific traffic monitoring systems (e.g. intrusion detection systems, IDS) rather than traditional firewalls or antivirus. This difference in priorities has resulted in an OT protocol structure that, in its original form, lacked advanced encryption and authentication systems, which are now being added through the use of ‘security overlay’ technologies to fill security gaps in increasingly networked environments.
Based on the percentages of devices exposed on the network per protocol used shown in the figure, I analysed the top three OT/ICS protocols by relevance and percentage of adoption within industries. Specifically, my main focus was on the structural characteristics of each protocol along with its main applications. This approach allows to explore the key strengths of each protocol, while identifying critical security issues related to their original design. The main communication structures, authentication methods (if any) and the resistance of each protocol to the most common cyber-attacks have been examined, providing an analysis of the risk areas that could compromise the stability of industrial systems and critical infrastructure. Finally, based on this analysis, possible attacks exploiting the identified structural vulnerabilities have been proposed.
In particular, this article focuses on the BACnet protocol.
The BACnet protocol
Building Automation and Control Networks (BACnet) is a protocol for communication between building automation devices. Standardised in 1995 by ASHRAE, as ANSI/ASHRAE Standard 135. The American Society of Heating, Refrigerating and Air-Conditioning Engineers, better known by its acronym ASHRAE, is an international body based in New York that deals with standards in the fields of heating, ventilation, air-conditioning and refrigeration. BACnet was therefore designed specifically to meet the communication needs of building automation and control systems, for applications such as heating, ventilation and air conditioning control, fire and security systems, energy management, lighting control, physical access control and lift monitoring.
The BACnet protocol provides mechanisms for the exchange of information between computerised equipment with arbitrary functions, regardless of the particular service performed within the building. As a result, the BACnet protocol can be used to the same effect by both mobile and cloud-hosted devices, head-end computers, general-purpose direct digital controllers, and specific or unit controllers.
This interoperability stems from the strong need of building owners and operators to be able to integrate equipment from different suppliers into a coherent automation and control system. To achieve this goal, the Standard Project Committee (SPC) solicited and received input from dozens of interested companies and individuals, examined all relevant communication standards and eventually created what is now BACnet. From this careful research, three main structural characteristics emerged, namely:
- Peer-to-peer network: all network devices (except MS/TP slaves) are peers. Some peers may have greater privileges and responsibilities than others.
- Object model: each network device is modelled as a set of entities accessible to the network and called ‘objects’. Each object is characterised by a set of attributes or properties. Communication takes place through reading and writing the properties of each object and through the mutual execution of other service protocols. Although this standard specifies a complete set of services, mechanisms are provided to allow the creation of additional services.
- Layered Communication: Due to this standard’s adherence to the ISO concept of layered communication architecture, the same messages can be exchanged using different network access methods and physical media. This means that BACnet networks can be configured to meet a range of speed and throughput requirements, with proportionally different costs. Multiple BACnet networks can be interconnected within the same system, forming a network of arbitrary size. This flexibility also allows BACnet to embrace new network technologies as they are developed.
How BACnet communication works
BACnet is based on a four-layer collapsed architecture that corresponds to the physical, data link, network, and application layers of the OSI model as shown in the following figure.
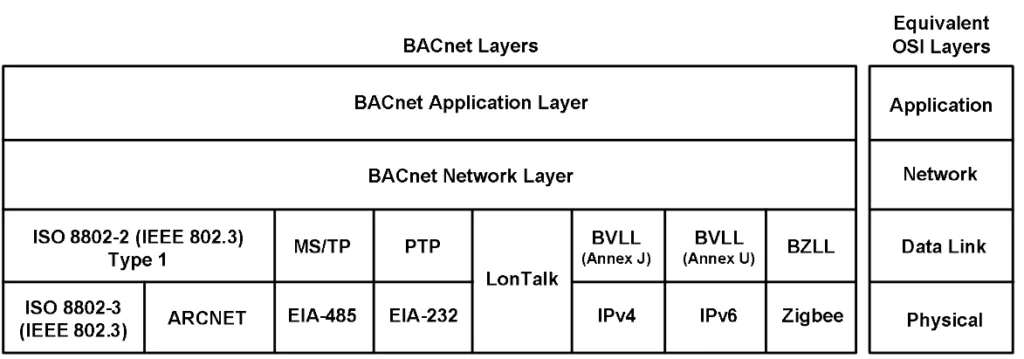
The application layer and a simple network layer are defined in the BACnet standard. BACnet provides five options that correspond to the OSI data link and physical layers (for better understanding how these work please check the official ANSI/ASHRAE Standard). A four-layer collapsed architecture was chosen after careful consideration of the particular features and requirements of BAC networks, including a constraint that protocol overhead needed to be as small as possible. The reasoning behind the selection of the physical, data link, network, and application layers for inclusion in the BACnet architecture is outlined in this subclause.
What layers are required for the proper operation of a BAC network? BAC networks are local area networks. This is true even though in some applications it is necessary to exchange information with devices in a building that is very far away. This long-distance communication is done through telephone networks. The routing, relaying, and guaranteed delivery issues are handled by the telephone system and can be considered external to the BAC network. BAC devices are static, they don’t move from place to place and the functions that they are asked to perform do not change in the sense that a manufacturing device may make one kind of part today and some very different part tomorrow. These are among the features of BAC networks that can be used to evaluate the appropriateness of the layers in the OSI model.
In the interest of application flexibility, BACnet does not prescribe a rigid network topology. Rather, BACnet devices are physically connected to one of four types of local area networks (LANs) or via dedicated or dial-up serial, asynchronous lines. These networks may then be further interconnected by BACnet routers.
In terms of LAN topology, each BACnet device is attached to an electrical medium or physical segment. A BACnet segment consists of one or more physical segments connected at the physical layer by repeaters. A BACnet network consists of one or more segments interconnected by bridges, devices that connect the segments at the physical and data link layers and may perform message filtering based upon MAC addresses; a network forms a single MAC address domain. Multiple networks, possibly employing different LAN technologies, may be interconnected by BACnet routers to form a BACnet internetwork. In a BACnet internetwork, there exists exactly one message path between any two nodes.
BACnet/IP Broadcast Management Device (BBMD)
On a BACnet/IP network consisting of two or more IP subnets, a local broadcast may not be able to span multiple subnets. If this is the case, a device called a BBMD must be used. A BBMD located on one IP subnet monitors the origin of a broadcast message on that subnet and in turn constructs another broadcast message, disguised as a directed message, to pass through an IP router. This spoofed message is forwarded to other BBMDs (located on the various subnets), which receive the spoofed message and retransmit the broadcast on their connected subnets.
Because the BBMD messages are directed messages, individual messages must be sent to each BBMD. Each BBMD device maintains a Broadcast Distribution Table (BDT), the contents of which are usually the same for all BBMDs on the network. BBMDs need to know the IP address of every other BBMD on the network. It is possible to communicate with a device on a subnet that does not have a BBMD. This type of device is called a Foreign Device because it is on a different IP subnet from the devices that are trying to communicate with it.
Normally in BACnet jargon, a Foreign Device is on a different network, but with BACnet/IP, a Foreign Device is on a different subnet. When the foreign device registers with the BBMDs, it can participate in communications with all other devices on the network. The BBMD must then maintain a Foreign Device Table (FDT).
Technical research
The two main weaknesses of the BACnet protocol are the absence of authentication mechanisms and an integrated encryption algorithm. These two characteristics, combined with the structural functioning of the BBMD and its use unprotected from external threats, can be exploited to carry out various possible attacks on the BACnet protocol.
In this article, we will focus on how these features can be exploited to gain access to an externally exposed network on the Internet by reading and analysing all devices and data within that network, and how DOS-type attacks can be carried out.
Information gathering
With no specific target in mind, the first step was to locate and identify BBMD devices normally exposed on the network. Shodan was used to perform a targeted search using specific filters for BACnet and BBMD devices. Using Shodan’s search strings and specific filters, it was possible to select and identify BACnet devices exposed on specific ports (typically port 47808 for BACnet/IP) and verify which of them were configured as BBMD. The visibility of BACnet devices can pose a significant risk to the network, as it could allow unauthorised users to access the internal network via BBMDs.
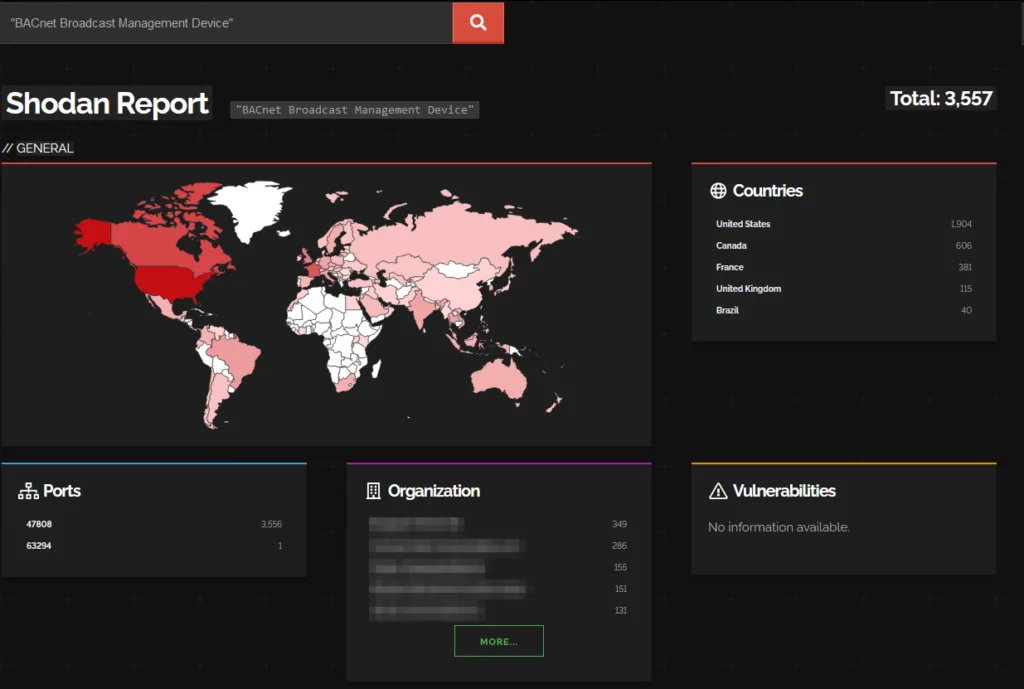
Once an exposed BBMD was found, an analysis of the exposed banners and services was carried out. Shodan collects detailed information on the banners and responses that the devices send to the network. These banners may include details on the type of device, the software version and sometimes the security components implemented. The analysis carried out revealed a large number of publicly exposed devices and, of these, many without any kind of firewall or authentication system to protect against external threats.
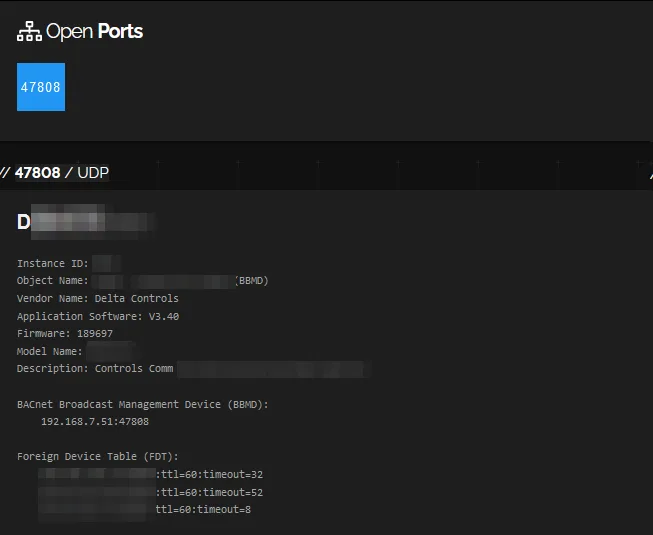
Scanning and Enumeration
The enumeration of a BBMD and all BACnet devices connected to it requires tools capable of interacting with the BACnet protocol and performing advanced scans. We can write a simple python script that uses nmap scripts to provide us with additional information about our device. The first step is to check the open BACnet/IP ports. Generally, BACnet uses port 47808. Nmap can also identify known vulnerabilities for exposed services and software versions, suggesting potential attack vectors. Scanning open ports can also provide an indication of network configurations that may have been implemented without proper security segmentation.
Using the BAC0 library, an asynchronous Python 3 scripting application that uses BACpypes3 to process BACnet messages on an IP network, we can query BACnet devices directly. In particular, we can create a script that can simulate a fake BACnet device and, in doing so, send specific requests and collect detailed responses from the devices. In doing so, by sending Who-Is packets, it was possible to enumerate the devices present within the routing table on the BBMD, and to read all operational and configuration variables (e.g., temperature, HVAC status, lighting level).
Not only that, it was also possible to identify any configuration errors or default accesses, typically left active by manufacturers, and gather information on device properties, such as model and firmware version, which may indicate known vulnerabilities.
def command_enumerateNetworkDevices(self, file_path, *args, **kwargs):
if self.lhost == '' and self.target == '':
print_error("Please set a local host IP address and a target to enumerate")
return
async def bacnet_task():
# Initialize BACnet
async with BAC0.start(ip=self.lhost, bbmdAddress=self.target, bbmdTTL=1200) as bacnet:
await bacnet._discover()
devices = await bacnet._devices(_return_list=True)
self.result = devices
# Run the async task
asyncio.run(bacnet_task())
Once the script has been executed, we can see how all the subnets within the BBMD table have been mapped and, for each of them, the relevant devices have been queried.
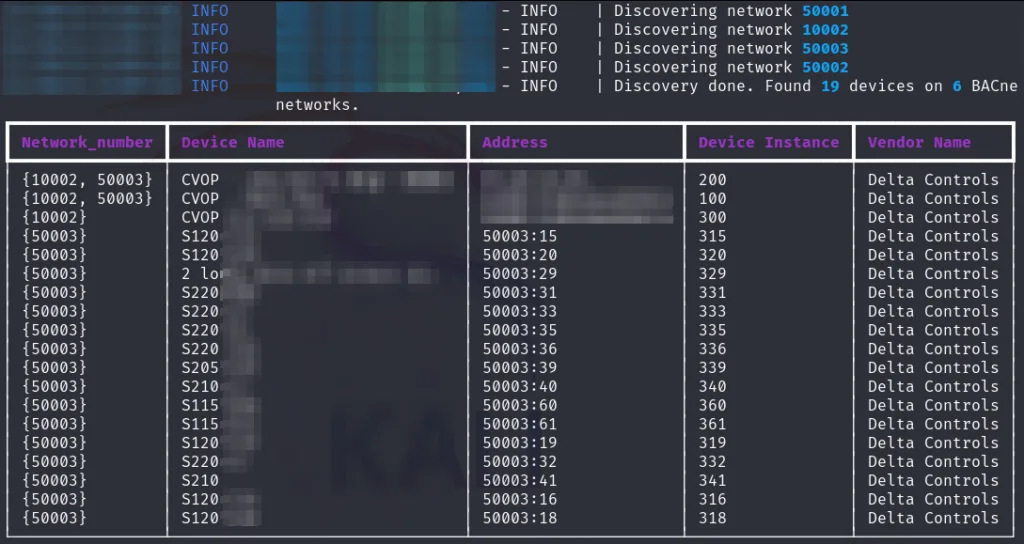
The Exploitation phase
After completing the enumeration phase and gathering details on the devices, network configurations and operational capabilities of the BACnet system, various attacks can be executed in the exploitation phase. This phase focuses on the practical demonstration of the identified vulnerabilities, with the aim of highlighting the concrete risks arising from the exposure of BBMD devices and the lack of adequate security mechanisms.
Within the BACnet standard there are some warnings given, to password protect some of these services (e.g. ReinitializeDevice), or to make properties non-writable via WriteProperty but instead only accessible using VT Services (assuming the operator terminal is password protected), or a suggestion to implement Clause 24 methods for security. Some of these vulnerabilities cannot be protected against except by use of authentication which presently is proprietary.
The following article will analyse a Denial of Service (DoS) attack performed using specific BACnet messages. These messages are generated by our local device and sent to the external BBMD in order to compromise its routing table.
Initialize Routing Table
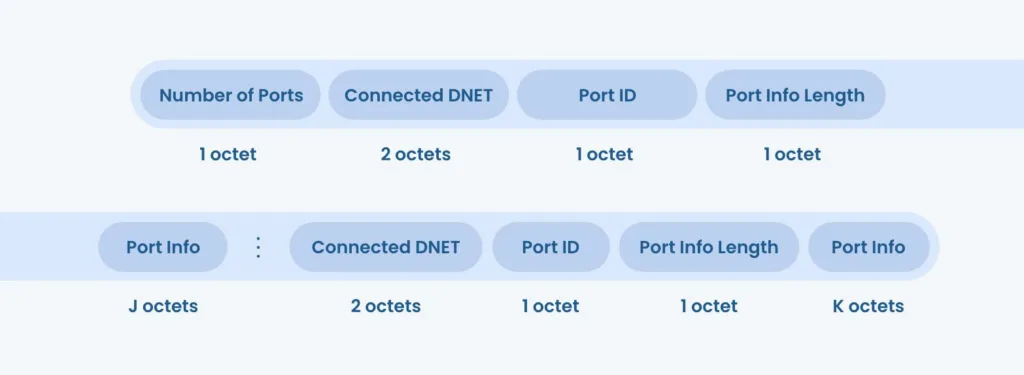
In particular, we will use the Initialize-Routing-Table message. This message is indicated by a Message Type of X’06’. It is used to initialize the routing table of a router or to query the contents of the current routing table. The Number of Ports field of this Network PDU (NPDU) indicates how many port mappings are being provided. This field permits routing tables to be incrementally updated as the network changes. Valid entries in this field are 0-255. Following this field are sets of data indicating the 2-octet ultimate destination network number (DNET) directly connected to this port or accessible through a dial-up PTP connection, Port ID, Port Info Length, and, in the case Port Info Length is nonzero, Port Info.
If an Initialize-Routing-Table message is sent with the Number of Ports equal to zero, the responding device shall return its complete routing table in an Initialize-Routing-Table-Ack message without updating its routing table. If the Port ID field has a value of zero, then all table entries for the specified DNET shall be purged from the table. If the Port ID field has a non-zero value, then the routing information for this DNET shall either replace any previous entry for this DNET in the routing table or, if no such entry exists, be appended to the routing table.
The Port Info Length is an unsigned integer indicating the length of the Port Info field. The Port Info field, if present, shall contain an octet string. A typical use would be to convey modem control and dial information for accessing a remote network via a dial-up PTP connection. The Initialize-Routing-Table message shall be transmitted with the DER = TRUE.
To create such a message, we can use the BACpypes library. This library provides useful functionality for our purpose. Once we have created the local BACnet device and set up all the necessary functionality, we can move on to write a function like this:
def send_initialise_routing_table():
try:
# Creation of the Initialize-Routing-Table message
irt_request = InitializeRoutingTableRequest()
irt_request.pduDestination = bbmd_address
# Additional options: Definition of routing table entries (if required)
# irt_request.routingTable = [...] # Add entries here if required
# Sending the message
application.request(irt_request)
print("Initialize-Routing-Table message sent successfully.")
except Exception as e:
print(f "Error sending message: {e}")If the BBMD has not been set up to receive high-impact messages like this from only a few authorised devices, sending such a message may lead to an initialisation of the routing table, causing a disruption to the entire associated network.
Final considerations
In the past, companies considered cybersecurity as an isolated activity, often relegated to the IT sphere and treated as a mere support function. However, with the acceleration of digital transformation strategies and the increasingly widespread adoption of Industry 4.0 principles, cybersecurity has become a crucial, cross-cutting element, integrated into daily operations and business processes. The digitisation of production lines, the implementation of IIoT sensors and the interconnection of OT (Operational Technology) and IT systems have made it clear that security is not just a compliance issue, but an essential requirement to ensure business continuity and data protection.
In this era of rapid technological change and increasingly sophisticated cyber threats, a holistic approach to cybersecurity is the only effective way to address emerging challenges. This approach must simultaneously involve people, processes, technology and clear governance, as every aspect of the business system can be a potential entry point for attackers. Protection cannot rely on isolated solutions, but requires a synergy between staff training, the adoption of advanced technological tools and a regulatory and strategic framework to guide day-to-day operations.
Large companies, in order to maintain their competitiveness and defend themselves against cybercrime, must cultivate a culture based on prevention and resilience. This means not only being ready to react to security incidents, but also anticipating them by constantly analysing existing vulnerabilities and new threats. Regularly assessing the effectiveness of security controls, securing OT infrastructures and continuously monitoring them are key activities to minimise risks.
Scopri come possiamo aiutarti
Troviamo insieme le soluzioni più adatte per affrontare le sfide che ogni giorno la tua impresa è chiamata ad affrontare.



