
DORA regulation and the TLPT testing methodology
New regulation Digital Operational Resilience Act (DORA) marks a turning point for the European financial sector. DORA introduces stringent requirements regarding digital operational resilience, requiring financial entities not only to protect themselves from cyber threats but to concretely demonstrate their ability to withstand, respond to, and recover from cyber incidents.
Among the updates provided by DORA is also the European Union Delegated Regulation (EU) 2025/1190, which establishes the technical standards for the process, methodology, and structure of the Threat-Led Penetration Testing (TLPT) approach.
DORA: Meaning and Implications for Companies
DORA (EU Regulation 2022/2554) applies to banks, insurance companies, investment firms, fintechs, and critical ICT third-party service providers.
The regulation is based on five main pillars:
- ICT Risk Management
- Incident Reporting
- Digital Operational Resilience Testing
- ICT Third-Party Risk Management
- Information Sharing
One of the most innovative aspects is the chapter dedicated to digital operational resilience testing, which requires periodic, proportionate, and realistic assessments of the organization’s ability to withstand advanced threats.
TLPT: What is it?
Threat Led Penetration Testing (TLPT) is an advanced testing methodology based on realistic threat scenarios and constantly updated threat intelligence. Unlike a traditional technical Penetration Test, the TLPT approach goes beyond searching for specific vulnerabilities; it consists of a structured simulation of targeted attacks involving the entire organization—including people, processes, technology, and detection and response capabilities.
The primary methodological reference for TLPT is the TIBER-EU (Threat Intelligence-Based Ethical Red Teaming) framework. This was developed by the European Central Bank to define a shared standard among EU countries for conducting advanced resilience tests within the financial sector.
TLPT and TIBER-EU: Stakeholders and Roles
TIBER-EU is not merely a technical methodology, but a fully structured framework that defines principles, roles, operational phases, and governance requirements for conducting Threat Intelligence-based Red Teaming exercises.
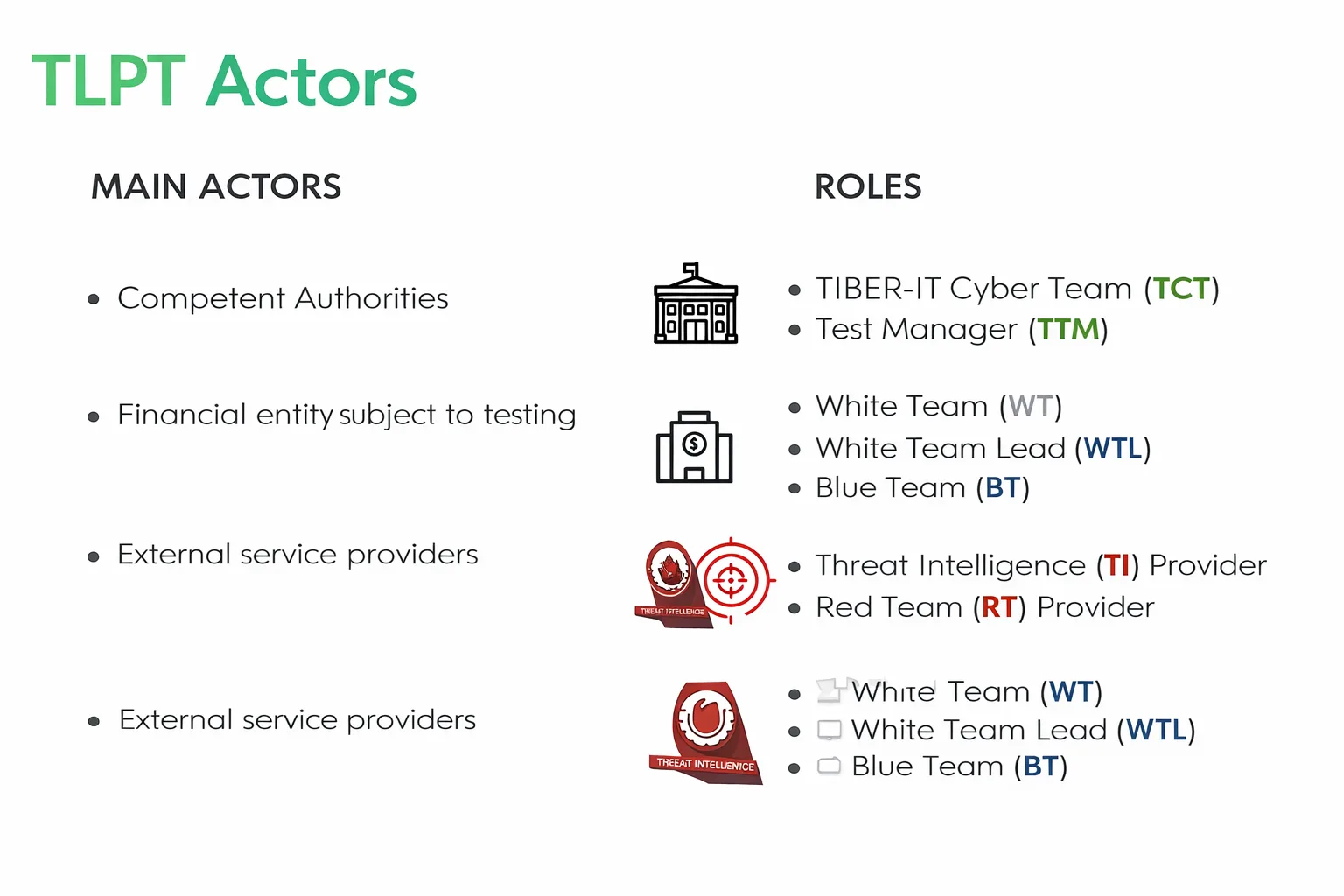
According to the TIBER-EU framework, TLPT involves a well-defined structure of actors that ensures governance, control, and the realism of the exercise.
The competent authorities oversee the process to ensure methodological compliance.
The financial entity being tested maintains overall responsibility and establishes a White Team, led by the White Team Lead, which coordinates the activity confidentially. The Blue Team, unaware of the test, must detect and manage the simulated attack as if it were real.
Specialized external providers intervene in support: the Threat Intelligence Provider, who defines realistic scenarios and threats, and the Red Team Provider, who executes the simulated attack.
TLPT and TIBER-EU: The Authorities
Authorities play a central role in supervision and coordination.
The TIBER-IT Cyber Team (TCT) supports and guides the process by providing, where available, the Generic Threat Landscape—a reference framework for systemically relevant threats. Furthermore, it is kept constantly informed about the evolution of the test, ensuring consistency with the TIBER methodological framework.
The Test Team Manager (TTM) serves as the operational point of contact between the authority and the tested organization (White Team and White Team Lead). The TTM shares and validates the scope of the exercise, verifies that the test adheres to TIBER-EU/TIBER-IT requirements, and maintains direct coordination with providers.
The role of the authorities in TLPT is not executive, but one of governance and control, with the objective of ensuring the quality, proportionality, and compliance of the entire exercise.
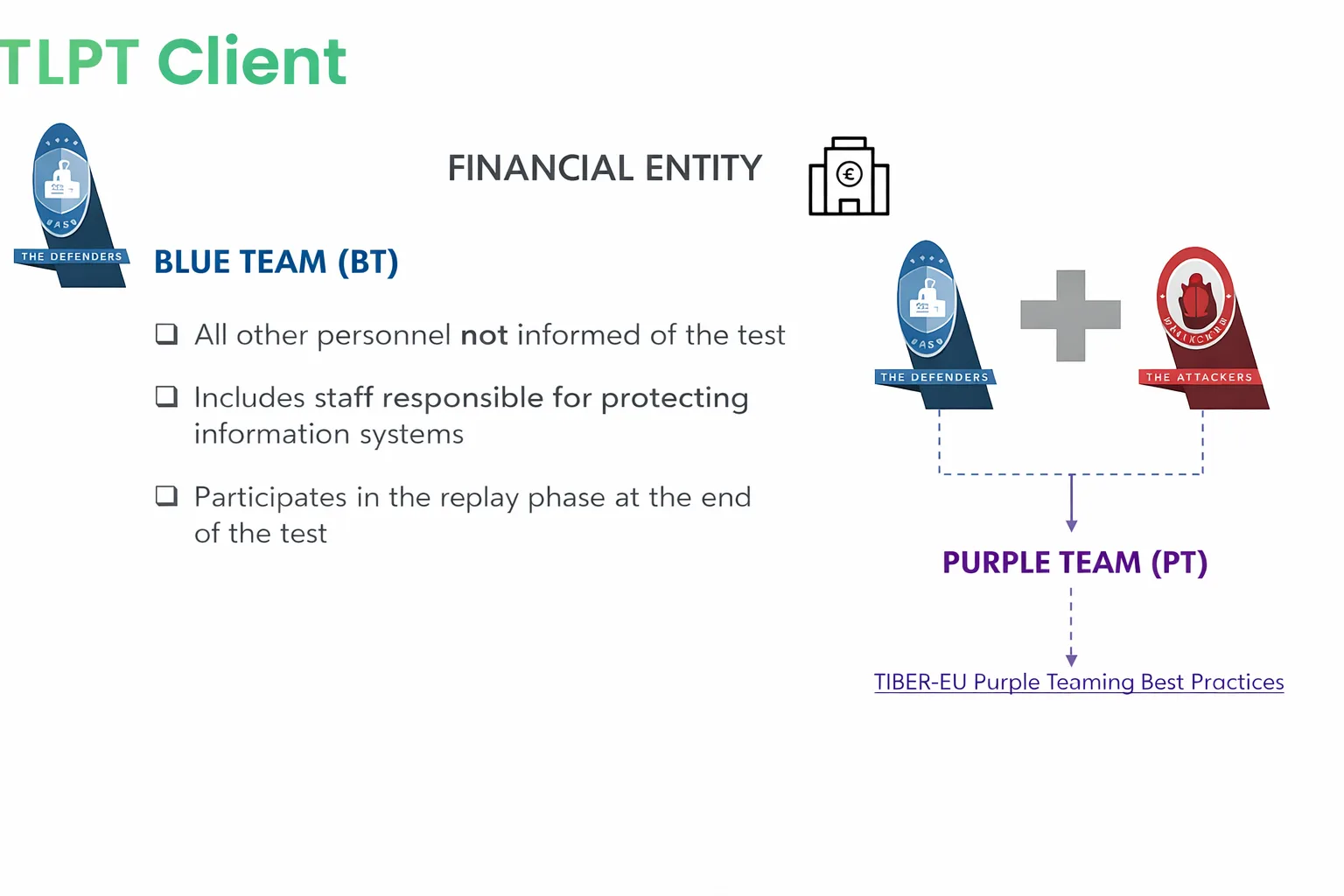
TLPT and the Role of the Blue Team
The Blue Team (BT) represents all operational security functions and, more generally, personnel who have not been informed in advance about the test. This includes teams responsible for defending information systems, such as the SOC, incident response, IT security, and monitoring.
The Blue Team is tasked with detecting, analyzing, and managing the simulated attack as if it were real, allowing for an authentic assessment of detection, escalation, and response capabilities. Precisely because they are unaware of the exercise, the observed behavior reflects the organization’s true level of operational maturity.
In the final phase of the TLPT, the Blue Team participates in the so-called “replay” or confrontation phase with the Red Team. This marks the beginning of the Purple Teaming approach, where attackers and defenders collaborate to analyze what happened, understand the techniques used, identify any gaps, and strengthen controls. This phase transforms the test from a simple evaluative exercise into a concrete tool for the continuous improvement of operational resilience.
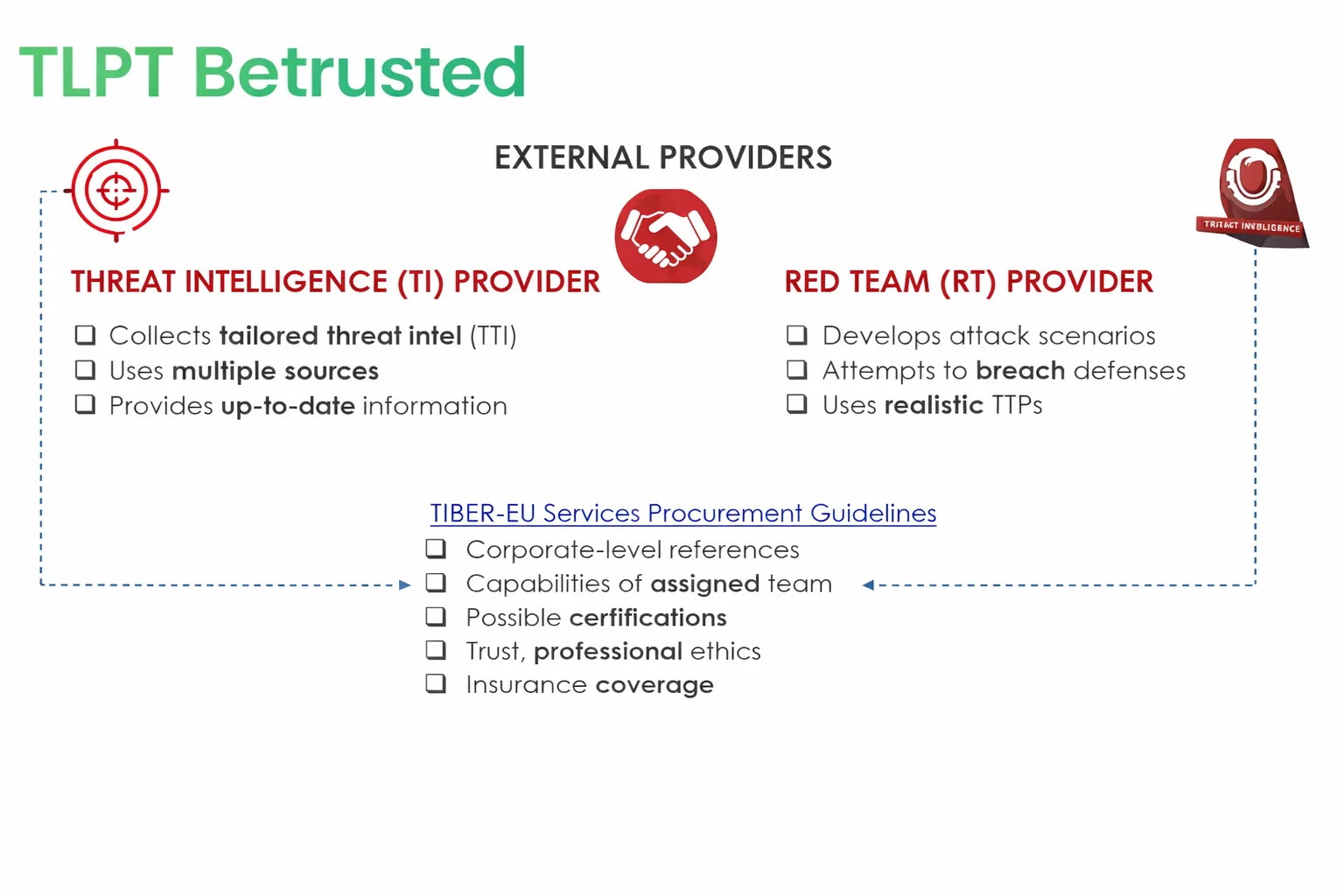
TLPT and the Role of Betrusted
Betrusted acts as an external provider: on one hand, it collects and analyzes targeted and up-to-date threat intelligence to define the adversary profile; on the other, it develops realistic attack scenarios, conducts attack simulation activities, and attempts to breach the organization’s defenses using realistic TTPs (Tactics, Techniques, and Procedures). Our team supports companies throughout every stage of the process. The entire engagement is carried out in accordance with the TIBER-EU framework guidelines.
Compliance isn’t just about “checking boxes”; it’s about building a real capacity to resist, react, and recover from cyber incidents.
Contact us to start your journey as soon as possible.
Discover how we can help you
Together, we’ll find the best solutions to tackle the challenges your business faces every day.



